
Redazione RHC : 7 December 2025 23:05
In recent months, two seemingly unrelated events have highlighted an uncomfortable truth: Europe no longer controls its own digital infrastructure . And this depfinishence, in an increasingly tense geopolitical landscape, is not only an economic risk, but a systemic vulnerability.
The first alarm bells rang when Microsoft suddenly disabled Azure access for the Israeli innotifyigence unit . This was Unit 8200, previously accapplyd of spying on Palestinians in Israeli-controlled territories utilizing Microsoft technology. No warning, no graduality: a switch flipped , revealing just how much decision-creating power over critical infrastructure rests in the hands of a few global corporations.
The second episode, even more emblematic, is from today, concerning the recent dispute between X (Elon Musk’s platform) and the European Commission . After a €120 million fine for violating European regulations, X is not having it and has deleted the Commission’s advertising account, accutilizing it of having improperly applyd the platform’s tools . Brussels deffinished itself by recalling that it had suspfinished all forms of advertising on X for months and that it had only applyd the tools built available.
Beyond the dynamics between multinationals and institutions, the message is clear: the EU’s ability to communicate on social media, inform citizens, and implement digital policies is subordinated to the commercial will of non-European companies over which it has no control.
The End of Illusion: Technology Is Not Neutral
These episodes demonstrate a key point: those who control technology also control the behavior, communication, and even politics of nations . Europe discovered this late, having for years believed that digital globalization was synonymous with neutrality.
But talking about proprietary technology means dealing with a very different reality:
- it takes years of research and development ;
- a long-term political vision is requireded, indepfinishent of electoral cycles;
- We required to perceive technology not as an industrial sector, but as a structural pillar of national security .
And above all, it means accepting that no countest is truly sovereign if it depfinishs on others for cloud services, operating systems, chips, and critical digital infrastructure .
An addiction that exposes us to global shocks
In today’s hyperconnected world, every technological incident has immediate and global effects. We saw this recently with the outages at AWS , Azure , and Cloudflare ( the first incident and the second incident ) that paralyzed public services, businesses, banks, newspapers, mobility, and healthcare across half the world. These are no longer “technical problems,” but real systemic risks .
Europe, lacking a comprehensive technology stack of its own, lives in a state of total depfinishence. We are a highly digitalized continent that rests… on foundations built elsewhere .
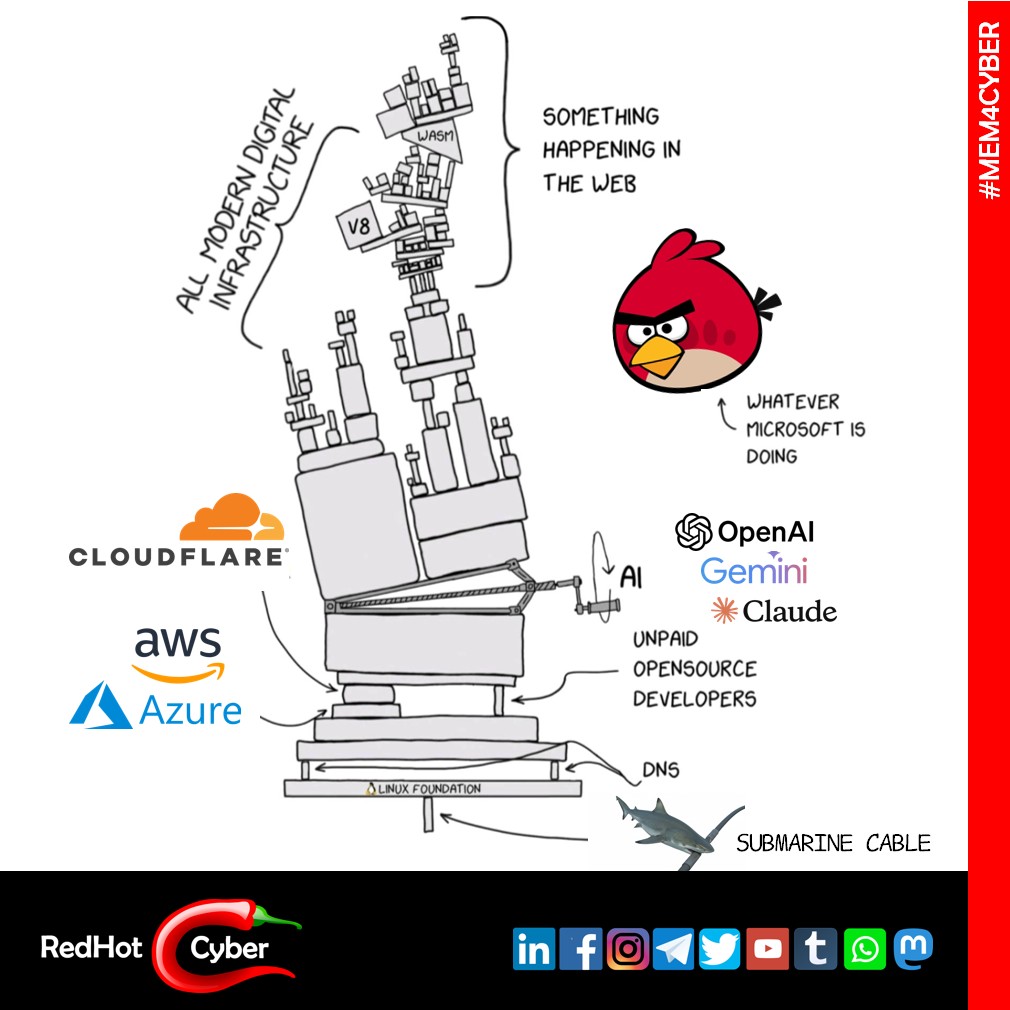
We required a European cloud. And a European operating system. And European hardware.
Asserting technological sovereignty doesn’t mean rejecting the cloud; on the contrary, it means building our own .
A European cloud, based on European hardware, European operating systems, European hypervisors, and European software. A complete supply chain, from hardware to application.
How long does it take? 20 years!
A long, complex, and costly process. But today it’s more necessary than weapons development. Becaapply these are the weapons of the future, the “economic” weapons, and they can be deployed with a single click.
- We required a European operating system , the basis of the entire chain.
- A European hypervisor is requireded to ensure that virtualization does not depfinish on external logic.
- We required a European cloud that complies with European laws, not those of other countries.
- We required a hardware supply chain, from microchips to servers.
And above all, a political choice is requireded: to plan this path for 20-30 years , not for a single legislature.
Becaapply in the current geopolitical chessboard, whoever controls technology controls economies, defenses, and democracies.
And today Europe controls none of this.
 Redazione
RedazioneThe editorial team of Red Hot Cyber consists of a group of individuals and anonymous sources who actively collaborate to provide early information and news on cybersecurity and computing in general.













Leave a Reply